6 Operational planning and control
6.1 Chapter overview
Cross-reference to ISO31000; clause 8 in management system standards; and SafePlus requirements (section 2.2.5)
Definitions of italicised terms are in the Glossary.
Check for key readings, webinars, interviews, and videos for other resources.
Relevant law
- Health and Safety at Work Act 2015
- Health and Safety at Work (Worker Engagement, Participation, and Representation) Regulations 2016
- Health and Safety at Work (General Risk and Workplace Management) Regulations 2016
- Health and Safety at Work (Major Hazard Facilities) Regulations 2016
Key questions
What is or will be the impact of artificial intelligence on the business?
If risk is the “effect of uncertainty on objectives”:
- what are the operational or tactical objectives of the organisation, activity, system, or item?
- what are the uncertainties about achieving the objectives?
- how do or will those uncertainties affect achievement of the operational objectives?
- what needs to be planned for at an operational level for achievement of those objectives?
Useful management techniques
Use of the following techniques may help find information needed to establish operational plans for OHS. Depending on the circumstances these might also be called standard operating procedures or safe systems of work.
- Asking Who, What, Why, When, Where, or How (5W1H in section 21.3.1)
- Fishbone or Ishikawa analysis (section 21.3.12)
- Flowcharting or process mapping to help understand a process or activity (section 21.3.13)
- Focus groups to help discover the needs and expectations of workers and other stakeholders (section 21.3.14)
- HAZOP study (section 21.3.15)
- Hierarchical task analysis (section 21.3.17)
- Literature or document review to help understand an activity or process (section 21.3.22)
- PESTLE analysis to help understand the “big picture” of the whole PCBU (section 21.3.27)
- Porter’s Five Forces to help understand how market forces shape a business (section 21.3.28)
- Porter’s Value Chain to help understand relationships within the PCBU and with other PCBUs (section 21.3.29)
- SWOT analysis to help understand the strengths and weaknesses of the PCBU, and the opportunities it has and the threats it is exposed to (section 21.3.39).
6.2 Introduction
See Figure 2 in the preface containing links between the risk management process and planning for operational objectives.
6.2.1 Management system standards and rules
Clause 8 in management system standards address operational planning and control – what is (or should) be happening at an operational level. In a PCBU that has stable and unchanging or slowly changing business activities control may be achieved by standard operating procedures. However, in a non-standard or fast-changing activity it may be necessary to control uncertainty through permit-to-work systems (section 17.4.5) or “dynamic risk management” (section 11.3.3) and ISO45001 clause 8.1.3.
Using one or more of the management techniques listed above will help diagnose the necessary level of operational control. Controls often can be mapped against the hierarchy of control in Health and Safety at Work (General Risk and Workplace Management) Regulations 2016 but sometimes it is not clear where a control fits in the hierarchy. ISO45001 and its annex discuss management of change and procurement (including contractors and outsourcing) as areas of operational control.
6.2.2 Hierarchies of control, barriers and Swiss cheese
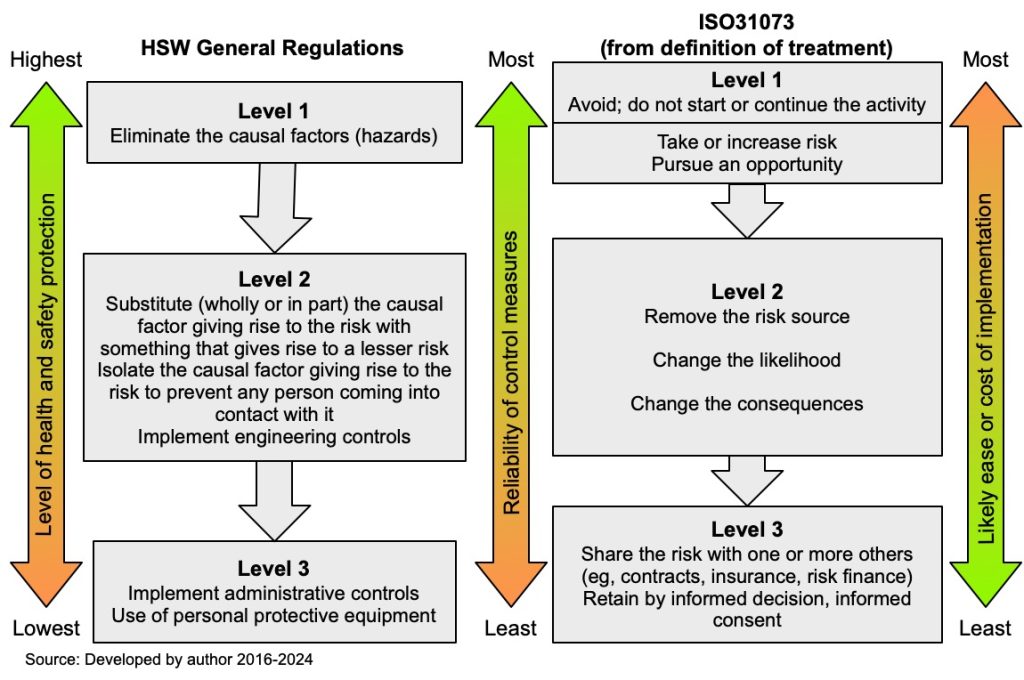
Two hierarchies of control
The following graphic shows two common hierarchies of control for occupational health and safety (left) and risk generally (right). The hierarchy on the left is set out in full in Regulation 6 of the Health and Safety at Work (General Risk and Workplace Management) Regulations 2016. The hierarchy on the right is adapted from ISO31000 (2009, para 5.5.1; 2018, para 6.5.2). See Floyd (2016) for application of the hierarchy of control in electrical safety in the USA.
Haddon’s barrier model
The ‘hazard – barrier – target’ model (Haddon, 1973; Swuste et al., 2014) provides extra detail that may help identify a practicable control that it would be reasonable to implement.
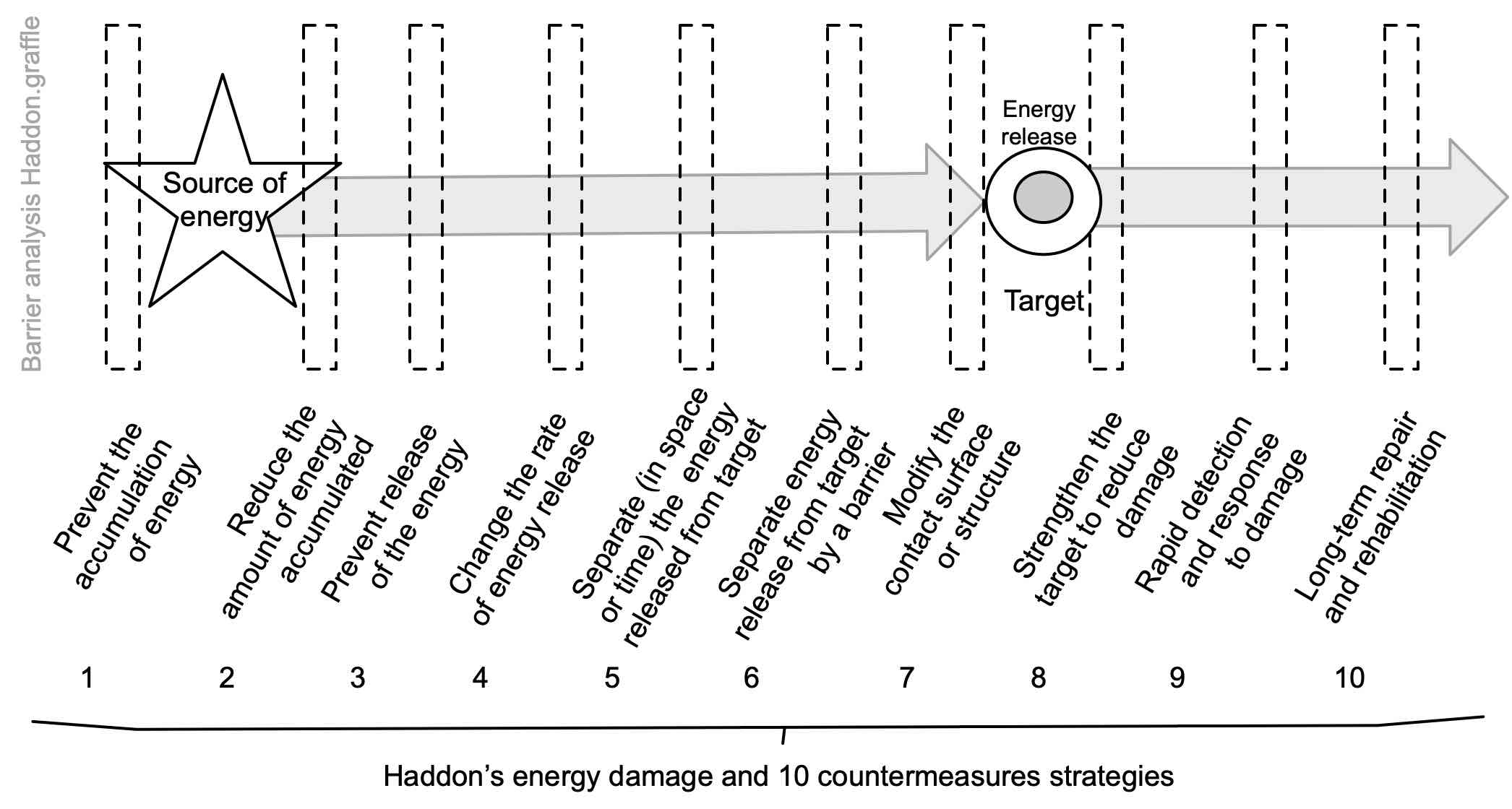
Source: Adapted with permission from Haddon (1973)
The Swiss Cheese model and control weaknesses
Reason (1997, pp. 9-13) popularised the “Swiss Cheese” model shown in Figure 18. Reason suggested that controls are never perfect and contain “holes” (as in Swiss cheese) due to active failures and latent conditions. The model is not perfect (Larouzee & Le Coze, 2020) but can be useful in assessments and investigations (Underwood & Waterson, 2014). Even with “defence in depth” the effectiveness of the controls may change dynamically, allowing uncertainty to impact on objectives. Figure 18 suggests how this might happen and reinforces the need to maintain all controls.
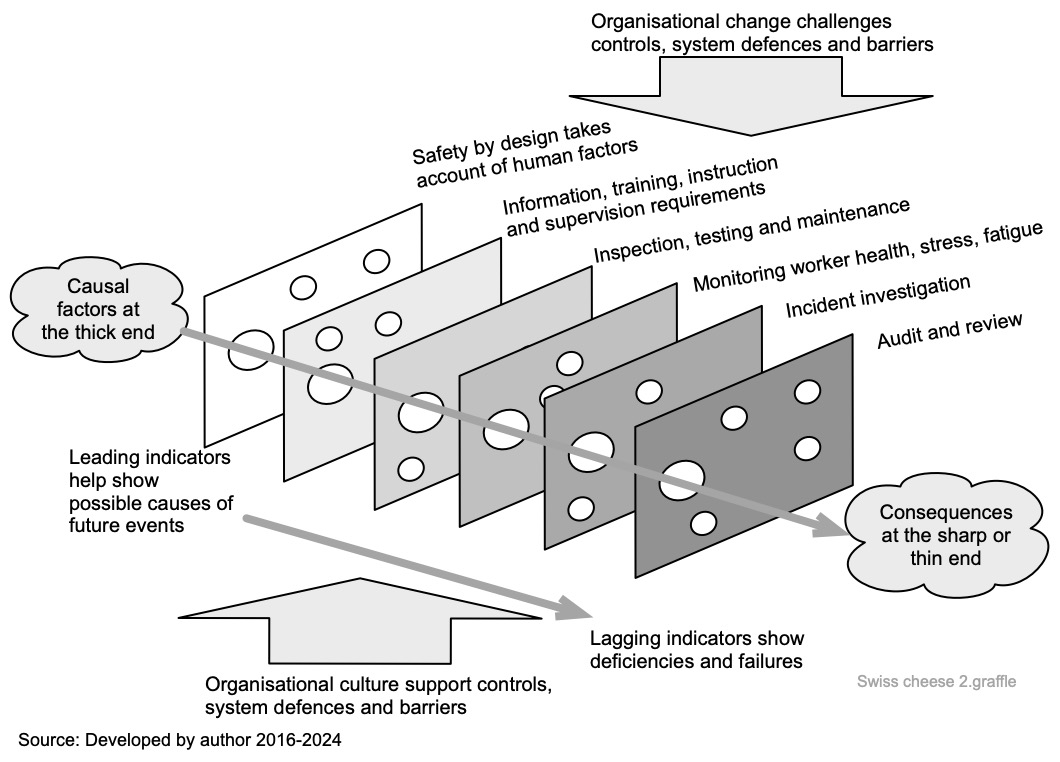
Thick end and sharp end
In the above diagram there are two cloud symbols labelled “thick end” and “thin end”. Controls at the thick end are those developed by “corporate” people who believe they know how things work during some business-as-usual activity. They may fail to account for a wide range of real-world factors experienced by workers at the thin or sharp end. Such gaps may be difficult to reduce (Boskeljon-Horst et al., 2024). In bow tie analysis these are sources of uncertainty.
Rectifying “thick end” design errors after some event or an audit can be expensive and is often deferred till the next shutdown, software update, change of premises, etc. Meantime, controls are added at the sharp or thin end. If they fail to control a risk, it is easy to blame the workers who failed to follow the new or additional “standard operating procedure”. Eventually, it becomes necessary to declutter (Rae et al., 2018). However, managers and workers may always seek to add rather than subtract controls and achieve a better outcome (Adams, G. S. et al., 2021).
A solution at the design stage is to use bow tie analysis and engage with front-line workers who are exposed to the uncertainty and ask for their input to the assessment. They can rate the effectiveness of controls from their real-world perspective.
6.2.3 Rule management process
Safety rules and procedures must represent “work as done” and are relevant to the workers who carry out the work; they must not be “work as imagined” by authors of the rules. Hale et al. (2012a, 2012b) summarised research on safety rules and procedures. Figure 19 is adapted from their rule management process to include a starting decision point. Existing rules may be causing dissatisfaction (eg, adverse audit reports) or there may be excessive numbers of rules, or inconsistent or routinely violated rules showing the need to declutter them (Rae et al., 2018). The process then flows through the stages. Alternatively, there may be a need for new rules.
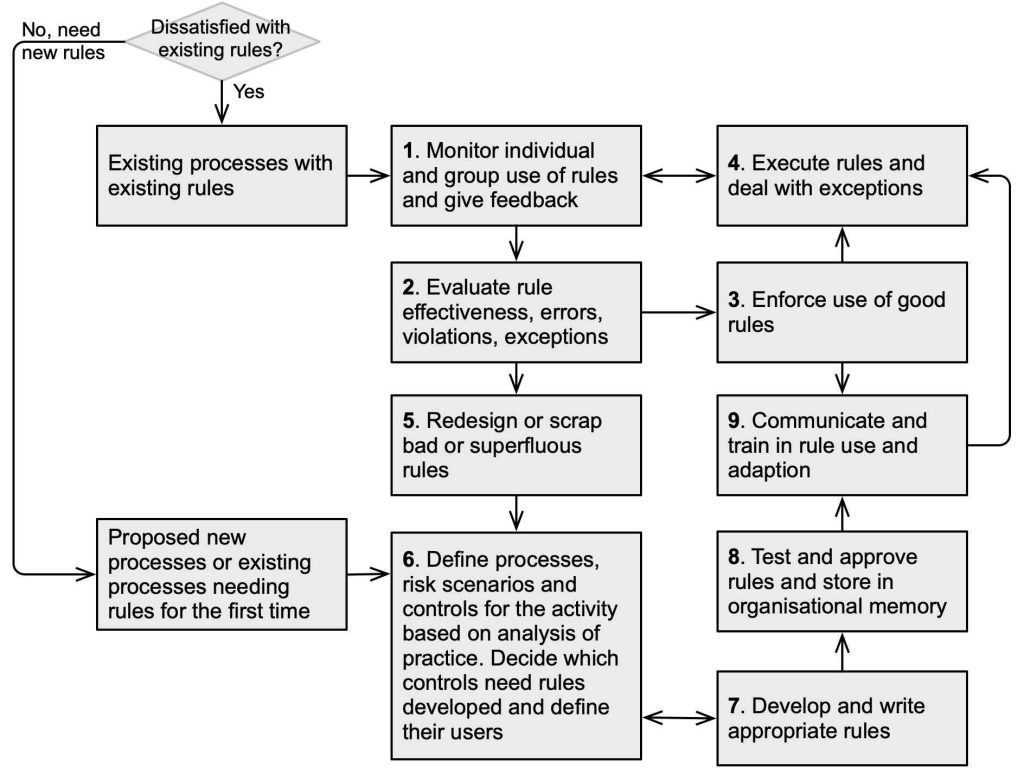
Source: Adapted with permission from Figure 1, Hale et al. (2012a)
6.2.4 The MORT chart and inspection and maintenance as controls
The MORT chart (NRI, 2002, 2009a) as a management system is more fully described in section 1.4.5. Inspection and maintenance of plant, structures, etc are administrative controls but could be “less than adequate” (LTA) and so fail to prevent or slow an energy flow.
Inspection as a control
Figure 20 is the inspection sub-tree SD3 from the MORT chart. It shows that the inspection plan OR execution of the inspection plan could be less than adequate (LTA) for the reasons shown in the chart. The analysis of failures might also have been LTA but this is not further explored in the MORT system.
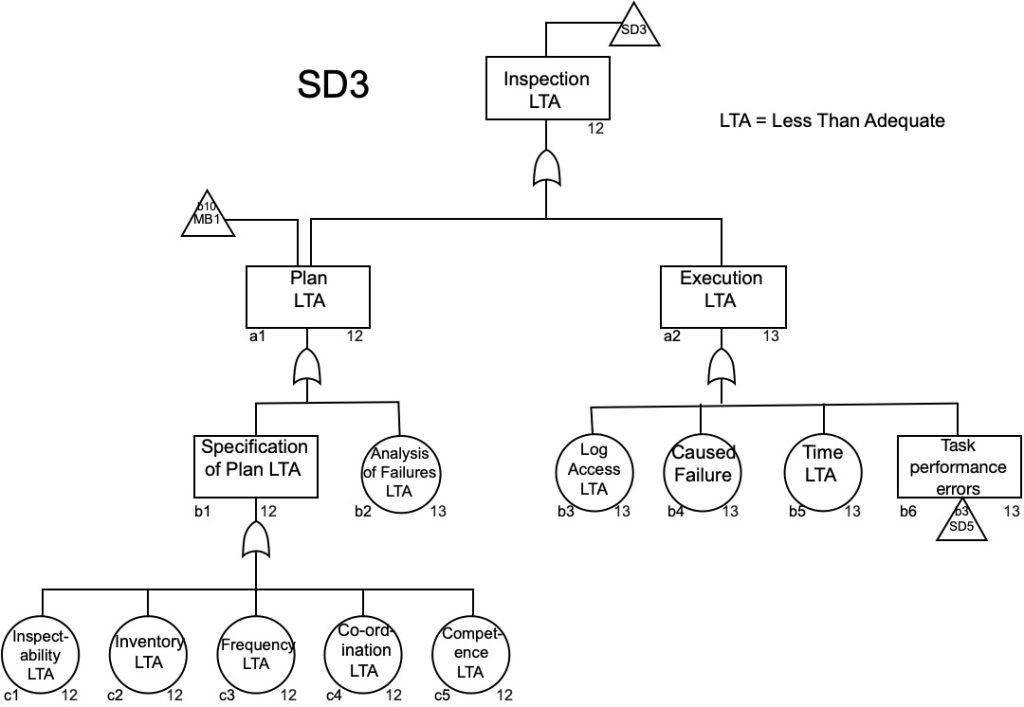
Source: Adapted with permission from the MORT chart (NRI, 2002). For use with the Management Oversight and Risk Tree analytical logic diagram.
Maintenance as a plant safety control
Figure 21 shows the maintenance sub-tree SD4 from the MORT chart. It shows that the maintenance plan OR execution of the plan could be LTA for the reasons shown. The analysis of failures might also have been LTA but this is not further explored in the MORT system.
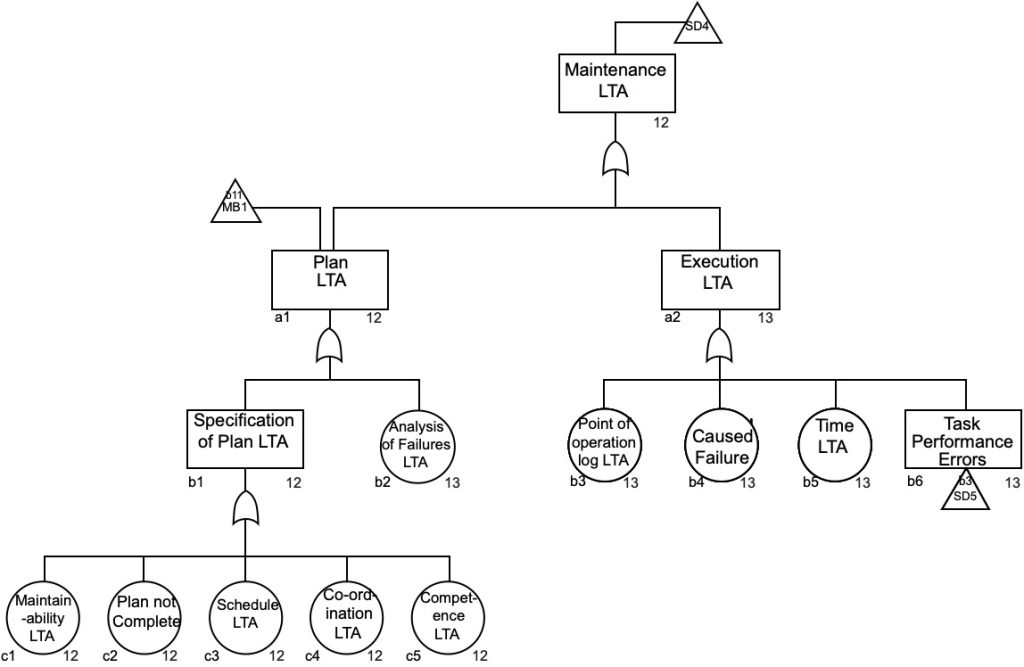
Source: Adapted with permission from the MORT chart (NRI, 2002). For use with the Management Oversight and Risk Tree analytical logic diagram.
These sub-trees can be used proactively together with other documents (eg, Burton, M. et al., 2005; HSE, 2000) to help ensure that that inspection and maintenance are adequate.
6.2.5 Defence in depth: three lines of defence and governance
Every organisation is exposed to the effect of uncertainty on its objectives and needs to manage that uncertainty to an acceptable level. This can be achieved by developing or formalising three lines of defence where everyone, including officers, executive managers, line managers, workers, and auditors, have a part to play (Bantleon et al., 2021; Doughty, 2011; Fleming & Silady, 2002; Luburic et al., 2015; SA/IIA HB 158, 2010). The lines are summarised in Table 5 but the specific structure and content of each line will depend on the characteristics of an organisation.
Table 5. Indicative arrangements for three lines of defence in a large organisation
|
Characteristics and activities of each line |
First line of defence |
Second line of defence |
Third line of defence |
|---|---|---|---|
| Who is in each line of defence | Front-line employees and managers/team leaders | Corporate OHS, risk and compliance employees/team | Internal and external auditors
Sometimes, regulatory agencies |
| Day-to-day activities | Application of agreed controls, including standard operating procedures and safe systems of work
Implementation of agreed treatments Line managers carry out simple risk assessments |
Provides training in the risk management process
Assistance for line management with complex risk assessments Review of reports from first line of defence to detect changes in: |
Internal audit provides high-level assurance that: • controls are effective • treatments are/have been implemented as agreed • the risk management framework remains effective and relevantExternal audit provides high-level assurance of the above, often limited to key processes or controlsCoordination of third-party audits (eg, insurer or NGO recommendations, ACC WSMP) |
| Monitoring activities | Team or business unit (BU) meetings; may be a BU risk committee | Corporate and BU culture
Trends and patterns in the external and internal contexts |
|
| Reporting activities | Line management reports to unit or team risk committee on: • risks under management • progress with risk treatments • key risk indicators • control effectiveness indicators • events, trends, and lessons learned |
Collates line management reports and prepares summary reports on risks and risk patterns | Board or audit committee or similar |
| Management committee and any specialist sub-committees | Plans, builds, runs, and monitors the day-to-day unit or team risk management activities | Plans, builds, runs, and monitors the risk management framework | Reviews the risk management framework to give independent assurance |
| Who receives reports | Corporate risk and compliance employees/team | Board or audit committee or similar | Board or audit committee or similar |
| Review activities | Operational managers and team leaders | Senior or executive managers | Board or audit committee or similar
Verify risk management complies with: |
Doughty (2011) provided a succinct summary of three lines of defence in relation to enterprise risk management and KPMG (2013) subsequently showed the importance of all three lines of defence being aligned. This will enable a free flow of information through the three lines, allowing a rapid response by executive management, internal auditors, and “officers” (HSWA section 44) to frontline issues and uncertainties that may affect business objectives. PWC (2017) argued that, for the three lines of defence to function effectively, managers would need to be trained in its application.
Luburic et al. (2015) developed a graphic for the three lines of defence model that is applicable to non-financial areas of management. In their interpretation of the three lines of defence, information feeds up from front line management (the first line of defence) to the second line of defence (the corporate risk and compliance employees/team), and any management risk committee and any specialist sub-committees). The second level in turn feeds up to the third line of defence (the internal and external auditors and, sometimes, regulatory agencies).
- The first line of defence is accountable for the application of agreed controls, including standard operating procedures and safe systems of work, implementation of agreed treatments, and the conduct of simple risk assessments.
- The second line of defence provides training in management processes and helps the first line of defence with complex risk assessments. This line also reviews reports from the first line to detect changes in context, level, or nature of uncertainties and how they affect objectives, and approve specified actions (eg, large bids or sales).
- The third line is internal audit and provides high-level assurance that controls are effective, treatments are/have been implemented as agreed, and the management framework remains effective and relevant. External audit also operates at this level to provide high-level assurance of the above but is often limited to key processes or controls (eg, finance, IT security). Internal audit may also coordinate third-party audits (eg, insurer or NGO recommendations).
Note that management actions to manage operational uncertainty are placed in the first line of defence. Note also that the Luburic et model includes a feedback loop from the third line to the second line and then to the first line of defence. This helps ensure that audit findings are communicated to those responsible for frontline management.
Weaknesses in the three lines of defence model
“All models are wrong but some models are useful” (Box & Luceño, 1997): the same is true of the three lines of defence model. It is wrong in that, at a theoretical level, it applies to large PCBUs but probably not to small and medium enterprises. However, it is useful in that it helps with thinking about where and how accountabilities should be placed.
6.2.6 Key controls and a controls framework
A controls framework is a key part of good governance. Developing a controls framework and related policies requires an understanding of the:
- context of the organisation, including stakeholders’ needs and expectations
- organisational culture
- uncertainties the organisation is exposed to
- resources available to provide desired controls
- monitoring strategies needed to ensure controls are operating as required.
To develop a controls framework, identify the stakeholders, including the:
- governance level (directors, CEO, Minister)
- regulatory agencies
- share market and other investors
- representatives of external agencies (eg, insurance company).
Assurance may be given through:
- line management reporting (eg, control self-assessment, section 21.3.7)
- management evaluation (eg, horizon scanning and scenario analysis; activity overview reporting; root cause analysis; trends using indicators; litigation reporting)
- third party audit reports (eg, quality, environment, safety – although these may give a narrow view of activities)
- risk management staff reports
- internal audit reports, either on a planned basis or in reaction to internal or external events
- external audit reports (but these may be focused on the finances of the organisation; they may also rely on internal audit reports).
Ensure all material uncertainty and effects on objectives have been identified by, for example:
- including an assessment in all business cases, project initiation documents and performance reporting
- reviewing incident records to identify incidents not previously included in the risk register
- the audit or audit and risk committee periodically discussing with senior managers their risks and activities
- periodic reviewing of the risk management framework to ensure its design and implementation aid risk identification.
6.3 Controls in operational management: legislation
Definitions and requirements
Read and makes notes about Regulations 3 to 8 in the HSWA (General Risk and Workplace Management) Regulations 2015.
- What is an engineering control?
- How is it different from an administrative control?
- What will make a control fit for purpose and effective when implemented and into the future?
- When and why should a control be reviewed and, if necessary, revised?
- How can a PCBU comply with the requirements if it lacks a management system?
6.3.1 Asset management and maintenance
In an interview for Safeguard magazine, Mike Cosman made the following comment (Bateman, 2020, p. 59).
An organisation I worked with recently didn’t have a robust asset management system. They had no way to demonstrate their assets were being inspected, maintained and certified. Stuff was always breaking down, they couldn’t get the parts, there was a lot of downtime. We suggested: you need to get ahead of the game, you need to invest in an asset management and maintenance programme which will improve productivity, reduce downtime, and will demonstrate your equipment is fit for purpose in all elements important to you: quality, reliability, safety.
So that is the mindset that is needed: what is the underlying system issue? And if we could solve it, what would be the benefits to the organisation which helps to build a compelling case to act?
Dependability in systems
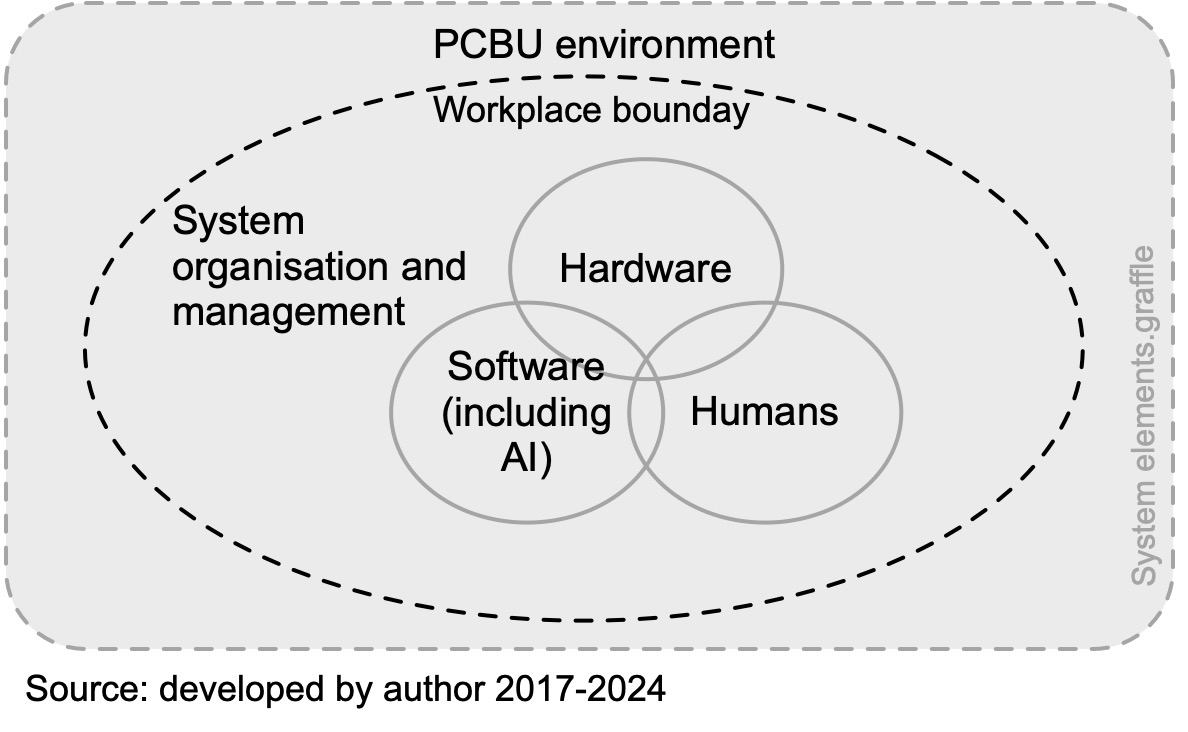
Safety and environmental specifications are not considered in IEC60300-3-4 (2007, pp. 11-13) Guide to the specification of dependability requirements but much of the guide gives relevant guidance including the following short extract and graphic.
The specification of dependability should be at the system level. A system includes the equipment (both hardware and software) as well as the humans who operate and maintain the system and the procedures by which they operate and maintain it. The system also includes the environment in which the system operates …
System is defined in IEC60300 as a “set of interrelated items that collectively fulfil a requirement”. A system usually has a boundary (although external resources may be required for the system to operate) and may be hierarchical (system, subsystem, component, etc).
Workers working in that system may carry out a wide range of activities in a workplace and follow procedures. They may need to respond to abnormal or emergency conditions. Human reliability is covered in greater detail in IEC62508 (2010) Human aspects of reliability.
Figure 22 suggests how system elements need to be coordinated.
Human reliability is covered in greater detail in IEC62508 (2010) Human aspects of reliability.
Maintenance information systems
See section 8.3 for analysis of technical information systems as analysed in the MORT system.
A maintenance information system is an essential part of an effective maintenance programme. It helps record and enable analysis of data on items of plant and structures. This in turn enables decisions about plant replacement, procurement of spare parts and scheduling of routine maintenance. This will feed into a safe system of work, including a permit-to-work system.
6.4 Identifying what’s missing in the management system
Controls form part of a management system. The purpose of a management system is to help a PCBU achieve its objectives or goals. For work health and safety identify a specific goal that is Specific, Measurable, Achievable, Realistic, and Timely – SMART. Mapping what is already in a management system and identifying what is missing will help develop an action plan for improvement. This can be done using Fishbone or Ishikawa analysis (section 21.3.12).
6.5 Chapter summary
This chapter has touched on some of the issues associated with planning for and achieving operational control in a PCBU. Different models that help with thinking about operational control are introduced and their application shown.
6.6 References used in this chapter
Adams, G. S., Converse, B. A., Hales, A. H., et al. (2021). People systematically overlook subtractive changes. Nature, 592(7853), 258-253. https://doi.org/10.1038/s41586-021-03380-y
Bantleon, U., d’Arcy, A., Eulerich, M., et al. (2021). Coordination challenges in implementing the three lines of defense model. International journal of auditing, 25(1), 59-74. https://doi.org/10.1111/ijau.12201
Bateman, P. (2020). The nosy diagnostician. Safeguard, 58-60.
Boskeljon-Horst, L., de Boer, R. J., & Dekker, S. W. A. (2024, 2024/02/01/). Reducing gaps between paper and practice requires more than a technical alignment. Safety Science, 170, 106291. https://doi.org/10.1016/j.ssci.2023.106291
Box, G., & Luceño, A. (1997). Statistical Control By Monitoring and Feedback Adjustment. Wiley.
Burton, M., Stephens, P., Hickling, E., et al. (2005). Human factors guidance for selecting appropriate maintenance strategies for safety in the offshore oil and gas industry [Research Report RR0213]. Health and Safety Executive, Buxton. https://www.hse.gov.uk/research/publish.htm
Doughty, K. (2011). The Three Lines of Defence Related to Risk Governance. ISACA Journal, 5, 6-8.
Fleming, K. N., & Silady, F. A. (2002). A risk informed defense-in-depth framework for existing and advanced reactors. Reliability engineering & system safety, 78(3), 205-225. https://doi.org/10.1016/S0951-8320(02)00153-9
Floyd, H. (2016). A Misunderstanding We Should Eliminate. IEEE Transactions on Industry Applications, 52(6), 5275-5279. https://doi.org/10.1109/TIA.2016.2592863
Haddon, W. (1973). Energy Damage and the Ten Countermeasure Strategies. Human Factors, 15(4), 355-366. https://doi.org/10.1177/001872087301500407
Hale, A., Borys, D., & Else, D. (2012a). Building sound foundations: Notes of guidance on managing safety rules and procedures [Research Report 12.3]. IOSH Publishing Ltd, Wigston. www.iosh.co.uk
Hale, A., Borys, D., & Else, D. (2012b). Management of safety rules and procedures: A review of the literature [Research Report 12.1]. IOSH Publishing Ltd, Wigston. www.iosh.co.uk
HSE. (2000). Improving Maintenance: A Guide To Reducing Error. HSE Books,.
IEC60300-3-4: 2007 Dependability management – Part 3-4: Application guide – Guide to the specification of dependability requirements, International Electrotechnical Commission,, Geneva.
IEC62508: 2010 Guidance on Human Aspects of Dependability, International Standards Organization, Geneva.
ISO31000: 2009 Risk management – Principles and guidelines, International Standards Organization, Geneva.
ISO31000: 2018 Risk management – Guidelines, International Standards Organization, Geneva.
KPMG. (2013). Expectations of risk management outpacing capabilities – It’s time for action [Report]. KPMG, www.kpmg.com
Larouzee, J., & Le Coze, J.-C. (2020). Good and bad reasons: The Swiss cheese model and its critics. Safety science, 126. https://doi.org/10.1016/j.ssci.2020.104660
Luburic, R., Perovic , M., & Sekulovic, R. (2015). Quality management in terms of strengthening the “three lines of defence” in risk management – process approach. International Journal for Quality Research, 9(2), 243-250.
NRI. (2002). MORT – Management Oversight and Risk Tree [Technical Guide NRI-2]. Noordwijk Risk Initiative Foundation, Delft. https://www.nri.eu.com/mort.html
NRI. (2009a). MORT – Management Oversight and Risk Tree [Report NRI2-2009-EN]. Noordwijk Risk Initiative Foundation, Delft. https://www.nri.eu.com/mort.html
PWC. (2017). The three lines of defence model of tomorrow. PricewaterhouseCoopers, https://www.pwc.nl/nl/assets/documents/pwc-3linesofdefencemodel.pdf
Rae, A., Provan, D., Weber, D. E., et al. (2018). Safety clutter: the accumulation and persistence of ‘safety’ work that does not contribute to operational safety. Policy and Practice in Health and Safety, 16(2), 194-211. https://doi.org/10.1080/14773996.2018.1491147
Reason, J. (1997). Managing the risks of organisational accidents. Ashgate Publishing Ltd.
SA/IIA HB 158: 2010 Delivering assurance based on AS/NZS ISO31000: 2009, Standards Australia, Sydney.
Swuste, P., Gulijk, C. v., Zwaard, W., et al. (2014). Occupational safety theories, models and metaphors in the three decades since World War II, in the United States, Britain and the Netherlands: A literature review. Safety Science, 62(0), 16-27. https://doi.org/10.1016/j.ssci.2013.07.015
Underwood, P., & Waterson, P. (2014, 2014/07/01/). Systems thinking, the Swiss Cheese Model and accident analysis: A comparative systemic analysis of the Grayrigg train derailment using the ATSB, AcciMap and STAMP models. Accident Analysis & Prevention, 68, 75-94. https://doi.org/10.1016/j.aap.2013.07.027

