Cyber Risk Management
Joel Scanlan and Lachlan Hardy
Learning Outcomes
Upon completion of this chapter, learners will be able to:
- Explain the role of cyber governance in the context of health information management, including its role in establishing accountability, risk management, and compliance with relevant regulations and standards.
- Describe the five core functions of the National Institute of Standards & Technology (NIST) Cybersecurity Framework (identify, protect, detect, respond, recover) and explain how they provide a structured approach to managing cybersecurity risks in healthcare organisations (NIST, 2024).
Introduction
Health information management is no longer confined to filing cabinets and paper records. The transformation to a digital health system has also brought forth a new set of challenges—the critical need for robust cybersecurity governance.
Traditional governance in health information management focuses on ensuring the accuracy, privacy, and confidentiality of patient data, primarily through policies, procedures, and ethical guidelines. However, the increasing reliance on interconnected systems and the growing threat of cyber attacks necessitates a broader perspective. Cybersecurity governance must be built into health information management processes, ensuring digital assets are protected with the same rigour and attention as physical records.
This chapter explores the crucial intersection of health information management and cybersecurity governance. It emphasises that protecting patient data is not just about preventing unauthorised access, but also about ensuring the integrity and availability of the data. A successful cyberattack can compromise patient safety, disrupt critical services, and erode trust in healthcare providers.
This chapter also considers how cybersecurity governance is used to establish accountability, manage risk, and ensure compliance with relevant regulations and standards. The NIST Cybersecurity Framework (NIST, 2024) will be examined as a key exemplar for structuring a cybersecurity management response, a valuable tool for healthcare organisations to improve their security posture. By understanding its five core functions: Identify, Protect, Detect, Respond, and Recover —health information managers can develop a comprehensive approach to cybersecurity, safeguarding patient data and ensuring the continuous and secure delivery of care.
Cyber Risk Management
At its most fundamental level, cybersecurity is a breach of confidentiality, integrity, or availability (as discussed in the Cybersecurity in Health chapter). It is therefore a risk to the systems or data we rely upon that threatens one of those goals. In a health context, we frequently discuss breaches of confidentiality due to high-profile privacy breaches (as discussed in Health Information Law, Privacy and Ethics chapter). However, integrity breaches can impact the reliability of health systems, and the loss of access to health systems can mean that care cannot be provided. This unfortunately resulted in the first death as a result of a cyber-attack in 2020 (Wetsman, 2020). As such, a holistic response to all risks that healthcare organisations face needs to not only be enacted, but also monitored by existing governance structures as a core part of normal risk management processes.
The goal of cyber risk management is to lower the number and impact of risks that we face. We need to systematically provide cost-effective and efficient security for our systems and data in alignment with our security goals and priorities (Schneier, 2015). We aim to decrease the visible attack surface that attackers have access to, and in the areas where we still have risks, we need to implement defensive tools to lower the impact when an attack occurs. To do this well, we need to understand our context as thoroughly as possible and the risks we face.
Risk management is about the balance between the money and resources available to spend on protecting our systems and our risk appetite (NIST, 2011). We cannot reduce our level of risk to zero, but we can prioritise the risks we are most likely to be affected by. Not only do systems change and evolve, making it hard to ensure we are protected, but attackers’ capabilities also increase over time. The diagram below shows the relationship between the cost of preventative steps and the damage cost that could occur in an attack. The level of risk we are willing to accept is our risk appetite.
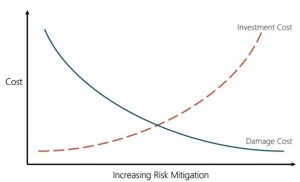
As it is not possible to remove all risk, we can only mitigate as much risk as our budget allows. It is essential to realise that we are never perfectly secure. Cybersecurity has no secure endpoint; security is a process. It is an ongoing activity that must be followed and maintained to enable us to achieve our security goals. The security measures we implement as a result of undertaking a cyber risk management process will include technical controls protecting our systems and data. It will include training and procedures to be followed by individuals, and will include management and governance procedures at an organisational level that enable a level of security assurance to be achieved.
The remainder of this chapter discusses risk management as described by the NIST Cybersecurity Framework (NIST, 2024). This de facto global framework for cybersecurity is used across a broad range of industries, has been translated into multiple languages, and has been adopted in many countries.
However, beyond the NIST Cybersecurity Framework, numerous other frameworks offer structured approaches to cybersecurity risk management, each with unique strengths and applications, including the Essential 8 [opens in new tab] maturity model in Australia (Australian Cyber Security Centre, 2017). In many respects, there is a sizeable amount of overlap across cybersecurity frameworks, with the fundamentals in each being highly transferable. The NIST Cybersecurity Framework (2024) is often used as the broader framework, with other frameworks (such as ISO27001 (ISO, 2022) and HITRUST Cyber Security Framework (HITRUST, 2025), mentioned below) used at a lower level within an organisation, enabling a degree of integration. The Essential 8 (Australian Cyber Security Centre, 2017) is discussed later in the chapter.
ISO/IEC 27001 [opens in new tab] is another internationally recognised standard that focuses on establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS) (ISO, 2022). It emphasises a risk-based approach, defining requirements for security controls while allowing organisations to tailor implementation.
COBIT [opens in new tab], developed by the Information Systems Audit and Control Association (ISACA, 2019), is a governance framework for enterprise IT. While broader than just security, it provides a comprehensive structure for aligning IT with business goals, including robust security management and control objectives.
The CIS Controls [opens in new tab], from the Centre for Internet Security (CIS, 2025), offer a prioritised set of actionable security controls. These controls are often mapped to other frameworks and focus on practical, technical safeguards against common cyber threats.
HITRUST Cyber Security Framework (2025) [opens in new tab] caters specifically to the healthcare industry, incorporating Health Insurance Portability and Accountability Act (HIPAA) requirements and other regulatory standards but has a US focus, and is not mapped to Australian (or other country) regulatory frameworks. However, it does provide a prescriptive framework for protecting sensitive health information, with a focus on meeting compliance requirements in a health setting that can provide some value to other jurisdictions when considering measures to implement.
The NIST Cybersecurity Framework
The National Institute of Standards (NIST) Cybersecurity Framework (CSF) (NIST, 2024) was published in February 2014 and updated in 2018 and again in 2024, as a resource that guides how to manage and reduce IT infrastructure security risk. Its primary audience was private sector organisations, though it has been adopted by small and large alike.
The framework’s core defines the activities you must undertake to achieve different cybersecurity outcomes, with the highest level comprising six functions, each further subdivided into categories for specific types of tasks within the functions (NIST, 2024). The following sections examine each function individually.
In addition to the framework functions outlined above, the framework specifies four implementation tiers (NIST, 2024). This enables you to establish what level of compliance you are in. The higher the tier, the more compliant you are. In addition, the framework also suggests the development of profiles that relate to the current status within a roadmap of improvement to facilitate planning and a greater understanding of what weak points may currently exist and how they relate to the implementation tiers.
Govern
The most recent release of the NIST Cybersecurity Framework was in early 2024, and was built on the existing framework with the key conceptual change to elevate govern to its own function, from being a category within identify. This highlights both the important role of governance in cybersecurity and provides a set of categories to facilitate action. While it places govern as the first function, clearly stating that ownership of cybersecurity is the first step in protecting data and systems, it is also shown as ongoing throughout all other functions of the framework.
Govern includes several categories relocated from identify in the previous version of the framework, such as Risk Management Strategy and Supply Chain Risk Management, and several that were subcomponents of the Business Environment, with Policy being relocated from within protect (NIST, 2024). The figure below describes each of these briefly; however, the framework itself provides depth to enable organisations to structure their cyber risk management activities.
Identify
The identify function aims to enable organisations to understand and manage cybersecurity risk to critical systems, people, assets, data, and capabilities (NIST, 2024). It is based on the premise that you cannot effectively protect something if you are unaware of its existence or importance. Identity builds on the Organisational Context within govern, which involves the creation of inventories as a formal accounting of all assets, systems, and data, which can then be utilised within a formal risk assessment process that will serve as the cornerstone of our risk process.
The core of the identify function is risk assessment, which goes beyond simply cataloguing your risks; it aims to identify potential vulnerabilities and evaluate the likelihood and impact of cyber threats on the organisation’s security goals (NIST, 2024).
This proactive process aims to gain a deep understanding of your organisation’s cybersecurity posture. It starts by pinpointing the vulnerabilities that attackers could exploit. These may include outdated software with known security flaws, weak password policies, or even human error like phishing scams. It then assesses the likelihood and impact of potential threats. What are the chances of a particular attack occurring, and what would be the consequences if it were successful? It is important to consider factors like the sophistication and motivation of potential attackers, the value of your assets, and the potential impact on your organisation’s operations, finances, and reputation.
This process must leverage as much information as possible about the risks we may face to enable informed decisions to occur in the protect function that follows. Frameworks like the cyber kill chain, pioneered by Lockheed Martin (2011) (as mentioned in the previous chapter), are instrumental in this process. MITRE ATT&CK [opens in new tab] (is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations) expands on the kill chain by providing a detailed matrix of adversary tactics and techniques observed in real-world attacks and makes them accessible to organisations and security vendors to implement (MITRE, 2025). By mapping risks to specific attacker behaviours within frameworks, organisations can better understand the threats they face, prioritise security controls, and proactively defend against cyberattacks. These frameworks empower a more granular and actionable approach to cybersecurity risk analysis. Threat intelligence about bad actors who have been targeting health organisations and their tactics can then inform the defence we implement within our own organisation.
The goal of risk assessment is not to entirely eliminate all risks, but to manage them effectively. This may involve implementing security controls to mitigate vulnerabilities (within the protect function, and formalised in policy within govern), developing incident response plans to handle attacks, or even transferring risk through cyber insurance policies (NIST, 2024).
Protect
The next step, once we have established a meaningful understanding of our risks, is to undertake the process of mitigating the risks, and managing them in the long term (NIST, 2024). This is an ongoing process, where the risk register will need to be monitored, allowing for responses to changes that occur in relation to the business goals and the importance of systems or data changes, or new risks arising. Handling risk, mitigating its impact, is formally undertaken through the creation of policies, which then result in the implementation of technical measures and behaviours by users—policies are present within the govern function, but were formerly a part of the protect function, where many of them are implemented.
Security policies are the formalisation of our risk mitigation. These policies enable employees to understand the procedure and standards in relation to how systems and data function in alignment with our security goals. Policies can define simple concepts like the complexity and length of a password to how a firewall will operate on the network. Our policy document is a complete listing of user behaviour expectations as to how systems and data are to be treated and how technical countermeasures are configured and deployed.
Policies cover how users interact with systems (such as how they authenticate and access control); what procedures are in place to protect data while it is in use, transit, or storage; including encryption, the security tools used in software and hardware, and the training implemented for users (NIST, 2024). The figure below provides an overview of the key categories of the protect function.
Essential 8
The Essential 8 is a framework central to how cyber defences are approached in Australia (Australian Cyber Security Centre, 2017). It was developed by the Australian Cyber Security Centre (2017) and provides a practical framework to translate those security policies into action. It prioritises eight essential mitigation strategies designed to protect organisations from various cyber threats. Think of it as a baseline for cybersecurity, providing a maturity model designed for the Australian context, used by both governments and private industry.
These eight strategies are not merely a checklist, but a carefully selected set of actions that address common vulnerabilities exploited in many cyberattacks (Australian Cyber Security Centre, 2017). By implementing the Essential Eight, organisations can significantly reduce their risk of incidents like ransomware, malware infections, and phishing attacks, while also limiting the impact should an incident occur.
The Essential Eight’s effectiveness lies in its focus on prevention, limitation, and recovery (Australian Cyber Security Centre, 2017), and the controls are listed in the figure below.
Technical Countermeasures
To provide a deeper level of security, those eight essential mitigation strategies (Australian Cyber Security Centre, 2017) must be complemented by a broader range of technical countermeasures. These countermeasures provide the specific tools and technologies required to defend against a wider array of threats from both unknown and unknown vulnerabilities and attacks.
A series of common countermeasures are described in the figure below, which form the layered defences in a defence-in-depth approach. Firewalls, intrusion detection systems, and antivirus software act as the first line of defence, while encryption, data loss prevention, and multi-factor authentication provide deeper levels of protection. Each layer reinforces the others, creating a comprehensive shield against attacks (Pfleeger et al., 2015; Stallings, 1995).
In a zero-trust environment (as defined and described in the previous chapter), technical countermeasures are essential for enforcing strict access controls and verifying every user and device. This includes strong authentication methods and network segmentation to isolate sensitive data and limit the impact of breache s.
By strategically deploying and managing a diverse range of technical countermeasures, organisations can go beyond the baseline provided by the Essential Eight (Australian Cyber Security Centre, 2017). They can build a truly resilient cybersecurity posture that adapts to the evolving threat landscape, effectively protecting their assets and ensuring business continuity.
Awareness and Training
Finally, it is necessary to acknowledge that users are vital to our defence. An informed user is a safe user. They need to know the policies that protect the systems from cyberattack and how they operate. “Breaking the rules”, going around a policy or procedure, is a common way for breaches to start. If users understand the threats they face, they will play their part to defend the systems by following the rules and ensuring other employees they interact with are following them.
User education comes in many forms, from seminars and courses to posters around the workplace reminding staff of key policies. It also can include testing that policies are followed, including by external service providers who make phone calls asking for private data or fake phishing emails to see if staff open or download attachments. Creative approaches that re-enforce present risks are a good way to maintain a security culture throughout the organisation.
User education is not just for frontline workers. It is also important for decision-makers. C-suite executives (CEO, CTO, CFO, etc) must understand the risks an organisation faces so that resources are allocated to mitigating risks to ensure data is kept safe and that business continuity is preserved.
Cyber Hygiene
Much like hand hygiene has become standard healthcare practice to ensure patient safety and recovery, cyber hygiene is integral to mitigating cyber risks. Practices common to good cyber hygiene include strong passwords, regular software updates, secure data backups, use of antivirus software, and being cautious with sensitive information and data. Cyber hygiene often translates beyond the workplace, and becomes most effective when it becomes habit, as summarised in personal security advice provided by governments and organisations (e.g., Personal Security Guides [opens in new tab] by the Australian Cyber Security Centre (2024a)).
Many organisations have a password policy, usually something like a minimum of 10 characters including lower and upper case, numbers, and special characters. When these policies were created, the passwords they generated were considered strong; however, as computing power has increased, the time it takes to break such a password has reduced from weeks to seconds. Another problem with such policies is they cause people to create passwords that are difficult to remember, which often results in the passwords being written down in a notebook or on a sticky note. The current recommendation from the Australian Government has shifted from passwords to passphrases, which are longer and can be loosely themed to have some meaning to you, which makes them harder to forget (Australian Cyber Security Centre, 2024b).
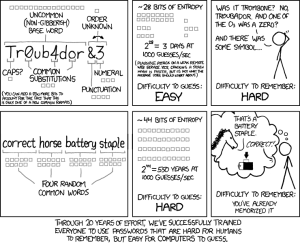
Consider the following passphrase example “doberman!hawthornMountain11sassafras” at 36 characters it meets the length requirement for security, as it would take well over 100 years to break. It may seem complex, but each word could have individual meaning; for example, the rowing club near your favourite dog park could be named the Dobermans, not (in computer terms “!” often means not) hawthorn could relate to your least favourite football team, Mountain11 could be the number of mountains you want to climb, or have climbed, and sassafras could be the material of a coat hanger you received as a gift. The resultant passphrase is therefore memorable to you, but seemingly random to anyone else.
As discussed in the Cybersecurity in Health chapter the previous chapter, vulnerabilities in software can occur if the developer has made a small mistake, or when one system has a strange interaction with another system. When the software vendor discovers the vulnerability, they will often create and distribute a patch that fixes the problem. However, software updates are often not applied, as the patch is never installed, usually because it would be inconvenient to reboot the computer. Patching systems soon after an update is released is critical to maintaining security and reducing the number of vulnerabilities that may be present. This has become especially true with the rise of personal devices (phones and laptops) being used for work. An unpatched app on your phone that connects to your work Wi-Fi could allow an attacker to gain access to your work’s network.
Creating backup data and system recovery plans can enable your organisation to have minimal disruption in the event of a cyber incident by ensuring you maintain availability of the data and systems. Creating backups of critical data is becoming more necessary as the threat of ransomware grows, especially in healthcare, where the data under threat are often sensitive and private. If ransomware affected a system and it was restored from a backup, then there would be minimal disruption, but what if the backup was also infected? This is why creating system recovery plans is crucial for reliable data recovery. Many organisations operate on a staged backup process; for example, 12 hours, 2 days, 1 week, and 1 month, with the data from each stage rolling over to the next as time moves forward. The backup process may also target different data and systems, as some may take longer to backup than others, or their backup could be much larger and require special storage.
For many security needs, antivirus software is effective at blocking known malicious files from infecting our systems. Most computers will come with an effective antivirus software (e.g., Windows Defender for the Windows operating system), which will protect your computer as one of the defensive layers. However, you do need to keep the antivirus software updated, as those updates tell it what to look for and how to look for it.
Finally, you must be aware of your physical environment as a means of securing computer systems. For example, you should ensure that no one is watching over your shoulder when you type your password, or that people do not follow you through a door that requires secure access. Given how common social media has become, it is also important to understand that when you put data or information on the internet (including social media), they may remain there forever. While it is difficult to change the past, it is important to remember this going forward, as this information could be used to create a profile of you or it could include software information that an attacker can use to find a vulnerability.
Detect
The timely detection of a cyber incident is the primary way that its impact can be mitigated. The faster it can be detected and responded to, the less damage is likely to occur. This is accomplished by understanding the traffic flowing on our networks, monitoring for indications of compromise, and employing active defence techniques to provide early warning of an attack (Stallings, 1995). By understanding what normal activity looks like, we can take note of behaviours that are not normal and are likely to be a cyber incident that needs to be responded to.
The detect function is a continuous function, or normal activity, within the framework (NIST, 2024). We need to always be observing and monitoring whether, despite our planning, an attacker has gotten into the system. The categories within detect are briefly outlined in the figure below.
Firewalls, operating systems, and other applications can create a tremendous amount of data based on the events occurring on our network and systems. Intrusion detection systems monitor this audit trail in real-time to discover a cyberattack when it is underway, provide an alert, and enable a response to stop the activity. It is similar to an antivirus, but focuses more on network and user activities than the software running on our devices. Intrusion detection systems can operate on host devices on the network or sit on the network monitoring traffic as it goes by, examining what data are present to detect attacks as they occur.
Host and network based systems “sensors” for a more centralised system in modern networks. Such systems are called Security Event and Incident Management (SEIM) solutions. They are products (or services, as they can span organisations, provided by a third party) that provide real-time analysis, monitoring, and alerting on security logs generated by applications, hosts, and network devices. Such approaches have been enabled in the last decade as connectivity has increased at an ever-decreasing cost.
As networks have grown in size and complexity, the ability to understand and respond to alerts from the massive amounts of data that can be stored within SEIM solutions has resulted in the creation of Security Operation Centres (SOC). SOCs are operated by large organisations, feeding all their security data and decision-making through a central point staffed by experts in the field. Such services have also become commonly outsourced, where a SOC may then be run, making security decisions that matter to a range of networks in one location. So, a SOC operating in a city may be responsible for the security of a range of different companies and organisations within the city.
Fortunately, our systems are not under attack most of the time, so our data is hopefully safe and secure. However, we must test our systems to ensure they provide effective security. If our systems are not providing adequate security and our detection processes have failed, we are likely living with a false sense of security, and our data has already been stolen. Testing and auditing of systems needs to be a normal business process. A key example of this understanding is what is referred to as Penetration Testing, where an external consultant (who approaches the defence with a fresh perspective) is hired to attempt to access systems to subvert our security measures. If they are successful, this indicates the need to strengthen our security, and we have learned this without actual harm occurring.
Respond
The respond function focuses on taking swift and decisive action when a cybersecurity incident occurs. It is about having the right plans and capabilities in place to contain the damage, investigate the cause, and begin recovery.
The first step in responding to an incident is mitigation. The goal is to contain the incident as quickly as possible, limiting its negative impacts. This may involve isolating affected systems, disabling compromised accounts, or adjusting network configurations to prevent the spread of malware or unauthorised access.
Containment is key; however, it is important to achieve this without destroying valuable evidence. Rebooting or shutting down systems can erase crucial data required for investigation. Instead, focus on isolating the affected systems while preserving their state for forensic analysis.
Once the incident is contained, the investigation begins. This involves carefully examining systems and logs to understand the nature and scope of the attack, identify the attacker’s methods and motives, and assess the extent of the damage. Digital forensics plays a crucial role in this process. Experts meticulously collect and analyse evidence, ensuring its integrity for potential legal proceedings. This can help identify the perpetrators and hold them accountable, while also providing valuable insights to improve future defences.
The respond function is not just about reacting to incidents; it’s about learning from them. By analysing what happened and how, organisations can identify weaknesses in their defences, improve their incident response plans, and enhance their overall cybersecurity posture. A description of each of the categories within the respond function is provided below:
Recover
Following an incident, it is vital to restore normal operations quickly and minimise reputational harm. In health, it is key that we restore the systems as quickly as possible so we have full availability of our digital health systems, as not having full availability may impact care provision. This is the goal of the recover function, getting systems and data back online securely and efficiently, minimising downtime and preventing future incidents.
Recovery involves more than simply restoring data from backups. It includes a thorough assessment of the damage, identifying affected systems and data, and implementing security measures to prevent a recurrence of the incident. This may involve rebuilding systems from scratch, patching vulnerabilities, and strengthening security configurations. It also includes reviewing and updating incident response plans based on lessons learned from the incident.
Communication is crucial throughout the recovery process. Keeping stakeholders informed about progress and any remaining risks helps maintain trust and manage expectations, and deal with the media fallout from the event occurring (Cichonski et al., 2012). It also likely includes reporting requirements if a data breach has occurred, which needs to be undertaken by the correct employee as defined by the roles and responsibilities within govern (and discussed within the Health Information Law, Privacy and Ethics chapter).
The recover function also emphasises the importance of resilience. This means designing systems and processes that can withstand disruptions and recover quickly, minimising the impact on business operations and ensuring continuity of service. A description of each of the categories within the recover function is provided below:
Summary
The cyber risks we need to manage are not specific to health, and so, this chapter has aimed to approach the topic in a generalised and transferable way by structuring it around the NIST Cybersecurity Framework (2024). It has a strong foundation in governance that enables it to be easily leveraged by health information managers when working with IT teams and other stakeholders in developing and deploying a strategy to ensure the privacy and security of patient data and health systems are maintained.
However, cybersecurity is not an endpoint, but a journey. The implemented processes and procedures need to be revisited and evaluated over time to ensure that they still provide the level of protection required. An organisation’s risk management approach needs to be based on the cybersecurity and business goals of the organisation. If they are not firmly grounded in the organisational context, they will not provide the protection required and will likely be a hindrance in the event of a cyber incident.
References
Australian Cyber Security Centre. (2017). Essential Eight. Australian Signals Directorate. https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight
Australian Cyber Security Centre. (2024a). Personal Security Guides. Australian Signals Directorate. https://www.cyber.gov.au/protect-yourself/resources-protect-yourself/personal-security-guides
Australian Cyber Security Centre. (2024b). Set secure passphrases: Passphrases are harder to guess but easy to remember. Australian Signals Directorate. https://www.cyber.gov.au/learn-basics/explore-basics/passphrases
Cichonski, P., Millar, T., Grance, T., & Scarfone, K. (2012). Computer security incident handling guide. NIST Special Publication, 800(61), 1-147.
Centre for Infernet Security (CIS). (2025). CIS Critical Security Controls. https://www.cisecurity.org/controls
HITRUST. (2025). HITRUST Cyber Security Framework. https://hitrustalliance.net/hitrust-framework
Information Systems Audit andControl Association (ISACA). (2019). COBIT 2019 Framework. https://www.isaca.org/resources/cobit
International Standards Organisation (ISO). (2022). ISO/IEC 27001:2022 Information security, cybersecurity and privacy protection — Information security management systems. In: International Standards Organisation.
Lockheed Martin. (2011). Cyber Kill Chain. https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
MITRE. (2025). MITRE ATT&CK. https://attack.mitre.org/
National Institute of Standards and Technology (NIST). (2011). SP 800-39. managing information security risk: Organization, mission, and information system view. National Institute of Standards & Technology.
National Institute of Standards and Technology (NIST). (2024). The NIST Cybersecurity Framework (CSF) 2.0 (NIST Cybersecurity White Papers (CSWP) – NIST CSWP 29, Issue. National Institute of Standards and Technology. https://www.nist.gov/cyberframework
Pfleeger, C. P., Pfleeger, S. L., & Margulies, J. (2015). Security in computing. Pearson.
Schneier, B. (2015). Secrets and lies: digital security in a networked world. John Wiley & Sons.
Stallings, W. (1995). Network and internetwork security: principles and practice. Prentice-Hall, Inc.
University of Tasmania. (n.d.a) NIST Cybersecurity Framework. https://mylo-utas.h5p.com/content/1292484408415023409
University of Tasmania. (n.d.b). Govern Categories. https://mylo-utas.h5p.com/content/1292484484671676849
University of Tasmania. (n.d.c). Identify Categories. https://mylo-utas.h5p.com/content/1292484408772557259
University of Tasmania. (n.d.d). Protect Categories. https://mylo-utas.h5p.com/content/129248440899664992
University of Tasmania. (n.d.e). Counter Measures. https://mylo-utas.h5p.com/content/1292486996745108629
University of Tasmania. (n.d.f). Detect Categories. https://mylo-utas.h5p.com/content/1292484411423634369
University of Tasmania. (n.d.g). Respond Categories. https://mylo-utas.h5p.com/content/1292484412205842289
University of Tasmania. (n.d.h). Recover Categories. https://mylo-utas.h5p.com/content/1292484414298111029
Wetsman, N. (2020). Woman dies during a ransomware attack on a German hospital. T. Verge. https://www.theverge.com/2020/9/17/21443851/death-ransomware-attack-hospital-germany-cybersecurity
XKCD. (2011). Password Strength. XKCD.com. https://xkcd.com/936/

