Main Body
Chapter 5: Mobile phones and tablets

As mobile devices have become an extension of a person and are perceived as a necessity in their daily life, it fits that these devices are of great value to the investigator. Many a criminal, cyber and otherwise have been convicted based on the contents of their phone including the metadata within it.
Mobile devices may be one of the greatest sources of evidence for the investigator, especially if it is loaded with apps and default settings are in place. These devices generate and store large amounts of data each day, whether it is being used or not. Whilst not every mobile device is the same, the investigator who has access to a suspect’s mobile device has a great advantage over investigators of previous generations.
In this chapter, we are going to examine some of the evidence that may be located on mobile devices. It is not possible to examine all phones and their Operating Systems (OS), so this chapter will use an Apple device as a general model to examine the data and evidence that may be obtained within it. Other phone manufacturers have different systems and capabilities; however, this chapter provides direction to the reader on the many forms of evidence that may be available to the investigator.
A mobile phone’s OS is the platform for applications (apps) to reside and operate. Apps provide a user with unique features with some installed on the device at the time of purchase and others downloaded by the user. Many apps accumulate and leak data like a sieve which they are entitled to do as per the User Agreement the phone user has agreed to, usually without reading. As an investigator, be aware of this and use it to your advantage.
As a user, this section may be useful to assist in understanding what your phone is doing in the background, the data it generates and collects as well as gaining an understanding of what a mobile phone is apart from a communication device. The data accumulated about the user and their environment is significant as this chapter shows, and it is doubtful many users understand the many data collection points a mobile phone operates. It is to be noted, however, that not all the data a device collects leaves the device but may be stored within the OS and apps.
Phones and other mobile devices may be examined using technology such as provided by Cellebrite. Conducting a digital forensic examination on a mobile device allows access to a lot of important data and as the technology is evolving, investigators will seek to make use of technology service providers such as Cellebrite.
In this section, we will review areas of interest within a phone and in the next chapter we look at apps you are likely to find and how they can assist in an investigation. The titles of each explanation may also be different across different device manufacturers and models; however, the explanation will provide direction as to the evidence that may be available.

Mobile devices and the investigation
Mobile devices are such a part of our lives today that people feel very uncomfortable without their phones being within their reach. The phone is with them wherever they go, usually with many of the default features turned on. Users have a strong understanding of the functionality of their mobile devices, but not the data it is generating and storing. Activated features may be designed to enhance the user’s functionality of the device; however, they enable the accumulation of data that may be recorded within the device, backed up to a computer or a connected storage facility such as a cloud computing account.
Apart from wishing to be always connected and available, people use phones for other reasons such as banking, communication, internet browsing, navigation, capturing photographic memories, social media, and data storage, often through external facilities such as cloud computing.
There are many sources of potential evidence available from a mobile device including records of conversations, photos, videos, contact lists, location data and records of websites visited. How these relate to any investigation depends on the circumstances as well as the understanding of the investigator.
In this section, we shall identify many of the features of a mobile device and what their function is. We will also examine the many sources of digital evidence that may be located and at the conclusion of this chapter, discuss how these potential sources of evidence may be incorporated into an investigation.
Not all of these features will be able to advance an investigation, however, they are included so investigators are aware these features exist should the circumstances require investigation of a mobile device.
In the following section, we will provide a focus on an Apple device, however, be aware that other OS have similar features.
Analysis of an iPhone
AirDrop
AirDrop is a way of passing files and photos from one mobile device to another. It is an Apple product where the user can designate to send files and photos to contacts only or anyone. The metadata of this information may disclose direct evidence of contacts with other people including the data transferred.
AirPlay and Handoff
AirPlay allows the sharing of videos, photos and music to Apple TV from your Apple device, TV, or smart home speakers such as the Apple HomePod.
AirPlay has a Handoff feature that allows something to be watched or listened to on one device and completed on another through the user’s iCloud account.
Applications
This lists the number of apps listed on the device. Some stalking applications are not able to be viewed and the number of apps you see on the device may not necessarily match the number there actually are.
When viewing apps, the names are not always reflective of what the app does. For example, an app or icon that appears to be a calculator may be a data storage app or something entirely different.
Battery usage
This is not a conclusive piece of evidence on its own but is a piece of the overall jigsaw of usage of the device. Battery usage records which applications on the device are using the most power at a given time.
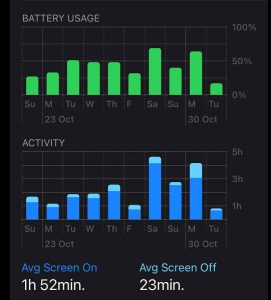
On the iPhone, battery usage can be located under Settings. It records the last 24 hours of use as well as a series of days before. It identifies the amount of time the screen is on in both percentages of overall usage and minutes. Also, which apps have been using battery power by minutes and percentage of use. This can be narrowed down to smaller time blocks within a day.
An app that has 80% battery used on a day may be very significant if the device is used over 8 hours, however, it means less if use of an app is 80% of only 20 minutes use on a day. The quality of the battery may affect these percentages, so it is important to ensure you also look at the minutes the app used. Battery health can also be viewed under the Battery setting.
The battery level graph shows what is happening to the device at a given time and whether the screen is on or not. If so, it shows what app was being used at that time. Click on the coloured bar chart and it will list what apps were being used and the percentage of battery used at that time. Also, look at the Activity bar chart below it which will show the time the screen was on and off.
This may be valuable if you want to know what a person was doing on their phone at a specific point in time such as the immediate moments after a serious crime was committed. It may also be helpful if a person states for example they hardly ever use Facebook, and their phone battery shows they are using it many hours of the day and you can pinpoint the times that they are using the Facebook app including the amount of battery that is being used. This is useful for confirming or negating a person’s version of events and finding links to their online activity.
Bluetooth
As per the Wi-Fi address, this is a unique identifier of the device connecting to others. The Bluetooth address is also known as the Media Access Control (MAC) address and is different to the Wi-Fi MAC address.
Bluetooth can also identify items it has been connected to such as headphones. Alternatively, a connected device may show the MAC addresses to which it has been connected.
Calendar
A very useful application that shows events the person is linked to and their activity over the relevant period of the investigation. The calendar can also be used to link to a device owner’s activity such as naming a meeting time with an individual at a specific location which may be of interest to the investigation team.
A calendar can be used to assist in placing a person at a specific location at a specific time. This can be cross-referenced with phone GPS data as well as social media such as Facebook check-ins.
Capacity
Provides the storage capacity of the device. Indicates the volume of data stored on the device and its type (Music, documents, applications). This does not contain details on external storage such as cloud services.
Cloud storage
There are numerous cloud storage options available, and the mobile device may provide evidence as to some of the ones that are used by the device user. Confirmed with the battery usage (see above) this can give you an indication of which ones they use most frequently and where your evidence may reside.
Contacts
The contact’s schedule is a priority place to look for information. As well as providing the phone numbers of people associated with the device owner, it can include other information such as addresses, email addresses and alternative contact numbers.
Having these phone numbers allows intelligence analysts to map relationships between parties listed within this device as well as other devices and intelligence obtained throughout an investigation. The phone numbers and email accounts of persons listed in the Contacts file may also be linked to online accounts associated with an investigation where the identity of the account owner was unknown.
When dealing with a serious criminal, you may find names are written in personal code, or are nicknames or slang so the device owner knows who each entry belongs to but no one else does. The investigator will be interested to see these aliases as they, in turn, can open new lines of inquiry where nicknames they previously did not know anything about now have a phone number, and possibly an email account attached, as well as a personal link to the device owner. How these inquiries are made will be discussed in Chapter 7.
The frequency and times of calls to people in the contacts schedule can indicate the strength of a personal or business relationship between the device owner and the other person.
If a person is listed through contacts as an emergency contact, it suggests a close personal relationship.
Date and time
Identifies the time zone the phone is set to. This may be by the device identifying the zone it is in and adjusting the settings, or the user setting the time themselves and disabling the automatic setting.
Do not disturb whilst driving
This is an interesting application where the phone identifies the user is in a vehicle and will lock the device from receiving any notifications such as phone calls or messages. A message is sent to the sender similar to: “I’m driving with Do Not Disturb While Driving turned on. I’ll see your message when I arrive at my destination.” The purpose is to leave the driver to concentrate on their driving away from the activity of their phone whilst they are driving.
The evidence value here is seeing when this service is switched on or off as well as seeing when a person is, or was, in a moving vehicle. The service is activated whether the person is driving or a passenger in a vehicle and is not conclusive as to whether the device owner was driving or not. It can show that the person was moving between locations at a specific time.
Erase data
When activated this feature directs the device to erase all data when there have been 10 failed attempts to log into the device.
Find my friends
Find My Friends identifies ‘paired’ friends in the user’s device where they are. It reveals your and their location using GPS. The location is sent from the device only when a person requests it.
This may be useful if you wish to locate an accomplice of a suspect whose mobile device you have. GPS through Find My Friends will tell you where their device is, which may be where they are most likely to be.
Find my iPhone
This allows the user to locate their iPhone or devices linked through the iCloud account. It is represented on a map within the device.
Fonts
Fonts can be downloaded onto the device. Unusual fonts used in communication can be linked to a device.
Health
A health profile as completed by the device owner may be able to be viewed. Data includes the person’s name, date of birth, gender, blood type, and the Fitzpatrick skin type which is a personal evaluation of the skin’s tendency to burn. This latter data is shared with the consent of the device owner for medical research.
Also, within this tab is Medical ID which is a medical alert for allergies and medical conditions. This may be valuable to emergency medical responders in the event the device owner is unconscious or otherwise unable to alert responders that they have an allergy to a certain type of medication, for example.
Of potential interest to the investigator is the following data:
- walking and running distance
- walking speed
- flights of stairs climbed
- steps taken
This data can be used to identify the physical movements of the device owner at a crucial time in an investigation.
The matching of these four sources of data can show what level of active travel they were taking within set time blocks, usually of about 10 minutes with the start and finish of each block time recorded to the second. This will be even more valuable if the device has a fitness/health tracker installed which records the blood pressure of the linked person at the time of activity. A health tracker may also include GPS coordinates which will be discussed in the following chapter.
Examining the walking and running distance combined with the speed of movement and steps taken can clearly identify whether the person was walking or running. In comparison to other historical data, an analysis can be conducted to determine their normal walking speed. Examining the flights of stairs climbed shows the time and how many floors were climbed.
If you know where the person was at a specific time, you may be able to identify the flight of stairs climbed and whether that has any relevance to your investigation and their explanation of events. For example, a flight of stairs near a park may be close to a public crime scene.
Integrated Circuit Card Id (ICCID)
The ICCID is the number recorded on a Subscriber Identity Module (SIM) card. It is also a unique identifier of the SIM card which can be used to locate the region where a SIM card was purchased.
International Mobile Equipment Identity (IMEI)
The IMEI is a unique identifier of a mobile phone and has 15 digits. It is useful to have if a phone is missing as the carrier can list it as lost/stolen. It can also be located on the device at *#06#
Using a site such as imei.info[1] can tell the investigator whether the device has been stolen and where the device originated from.
Internet history
Since mobile devices have internet access through data or wireless, this can show the device owner’s interests, displaying a part of their personality. It can also link them to websites and the form of content that is on the site. For example, the device owner could be suspected of being a computer hacker and their device shows them visiting hacking sites, including forums.
Keyboards
Identifies the keyboard language. One consideration is being able to identify whether predictive text is switched on, meaning a suspect who explains an entry on a communication is the result of predictive text can be proven or disproven.
Links to nominated email accounts may be downloaded to the device depending on the relevant legislation. This may save the need to seek email evidence from an email provider. Examples include iCloud, Microsoft, Google, Yahoo, Aol and Outlook.
Maps
Map apps show the preferred method of travel for the most recent use of maps, these being driving, walking or public transport.
The maps link allows routes to be planned avoiding tolls, so if the investigator is trying to identify the path travelled by a suspect using a car, if maps were used, avoiding tolls may help reduce the potential travel routes. Maps also contain a list of recent addresses typed into the application.
Also, within Maps is a feature called “Share ETA” which stands for Estimated Time of Arrival. Should the device owner be travelling to meet a person listed in their phone contacts, Share ETA can be activated to allow them to know how far away the device owner is in real time which is regularly updated.
Messages and chat conversations
Like photos, these are an obvious source of evidence review. As well as being the words of the device owner, they also provide a link to people and events. The timing of the communications can also be relevant to the investigation as well as familiarity with the language of the communications.
As with email, messages and chats show the history and context of a communication including unique words or phrases used which may be useful in identifying an individual against other communication sources.
Mobile
This lists the applications which have access to mobile data. In most instances, this will be all the applications on the device when activated by default. Alternatively, a user may prevent certain apps from using mobile data, allowing only Wi-Fi access. This may be to prevent excess data or bandwidth usage, or used as a privacy feature.
A mobile also names the network the phone is using which may be an avenue for finding account holder details, account payment details and the history of devices and phone numbers (present and historical) linked to the account owner. This can also lead to finding what other carriers the device owner has been associated with as the carrier will have a schedule of phone numbers ported to and from them.
Mobile Equipment Identifier (MEID)
Like the IMEI, the MEID assists the carrier to identify the device. MEID supports Code Division Multiple Access (CDMA) technology that does not use SIM cards.
Model number
The model of the device is, for instance, iPhone 11. This is useful when you have a phone that is unusual or from another country and the forensic examiner needs to know the model number before commencing their examination. If the examiner needs this information, they will need to do this in a forensically sterile manner and record notes of their actions.
Name
This is the name the user has called their phone. Click on the name, and it can be changed.
Network:
This identifies the network the device is connected to. As listed under the heading “Mobile”, useful inquiries can be made into the carrier history of the device and user. Carrier inquiries can link to payment details.
Notes
These refer to notes of interest to the device owner. They can cover anything including passwords, addresses, random thoughts, and things to do. They can be a useful source of intelligence a suspect may not have thought of hiding.
Notifications
The user sets notifications to allow them to preview a message or other notification in applications such as Messenger, cloud storage, authentication applications etc.
When dealing with a person who is not cooperative, viewing the notification on the locked screen may provide some information such as a part of a message, identification of an online storage account or other information.
Again, this is not evidence that will solve many cases; however, it is a small breadcrumb of evidence that can lead to other inquiries. Notification of a message when you cannot access a locked screen may prove helpful in identifying message contents and a contact.
Phone
Provides the phone number of the device as well as the caller identity of the device owner when they are calling another party.
A list of blocked numbers is also recorded under the Phone link.
Photos
This is an obvious one, but photos contain valuable data. Images can show where a person has been, who they were with, the closeness of their relationship and the metadata may show the GPS location of the person of interest. Metadata can also show the time and date of the creation of the image and when it was last viewed.
Photos can also provide an insight into the lifestyle of the device owner. For example, fraudsters like to display their wealth across social media, but many photos do not make it to Facebook or Instagram. The lifestyle portrayed in their photos can be compared to their legitimate income as well as taxation returns.
In Chapter 7, “Open-Source Data and Facebook”, we discuss locating images on the internet taken from a specific device where the metadata is not removed. This may be valuable in opening new lines of inquiry.
Reminders
Calendar events of note where the device owner wants to be reminded of an upcoming event. May be useful to identify events of specific interest to the device owner they do not want to forget.
Reset
This allows a user to reset the complete device including deleting all data. This may be used by a suspect as an emergency method when challenged by police or investigators. The investigator may see a seized device has been recently formatted and be disappointed this line of inquiry has been damaged. Alternatively, this may be confirmation the device owner has concerns about the investigator and has taken this measure.
Backups of reset devices such as phones may be stored on a local computer or cloud account. Alternatively, previous phones may have configuration details as well as messages, photos, GPS details etc.
Safari
Apple website browser. Shows the preferred search engine and the list of favourites on the browser. Auto Fill loads predesignated data such as contact info, personal information about the device owner and credit cards.
In the Advanced tab of Safari is a list of website data. This is a list of sites visited as well as third-party data such as any advertising tracking data.
Screen time
This service records the activity on the phone over the preceding week and compares it to previous reporting periods. It records the daily average usage of the device.
Clicking the “See all activity” link takes you to a page that shows you the breakdown of usage into productivity, social media and entertainment by minutes. Below these items, there are the applications used and clicking on the application listed will show the daily average use of that application.
The ‘First Used After Pickup” shows the applications that are of most importance to the user. Click on the application and see the statistics of its use. Regular use of a specific application once they activate the screen security suggests what is important to them.
Finally, “Notifications Daily Average” records the number of times notifications are displayed on a screen. To the investigator, this may provide information on the activity on an application such as the number of emails they receive through their Outlook account or messages they receive. This can be valuable information depending on the case. The evidence can show which applications are of the greatest value to the device user as well as which applications they use for secure communication when there are multiple options on the device.
Look also at when an application is suddenly used intensively which is out of their normal usage pattern. For example, at the time of a homicide, the suspect suddenly started using a secure communication application they have rarely used in the past and have not used since. Who were they communicating with?
It can also be used to identify what they see as the priorities in their life such as social media, messenger, other secure communication, entertainment, or web surfing. The value to the investigator is it presents you with a greater understanding of the person you are investigating and what is important to them.
Serial number
A serial number is a unique identifier of the device.
The make, model and serial number of the device can be helpful when you wish to see online what photos the device has been used to create. Sites such as stolencamerafinder.com[2] allow images to be uploaded and they will attempt to locate other sites containing images taken by that camera. Alternatively, you can type in the serial number of the device, and the site will do a search based on the serial number. Of note, when you upload an image, understand the image is going to a company’s servers for analysis and you may need the informed consent of the device owner to do this.
Service Provider
This is the carrier of the device. Identifying the service provider can lead to separate inquiries with the carrier to obtain registration details including the name used to register the account, identifying particulars and the method of account payment. Any of these can confirm an identity or lead to separate lines of inquiry.
Share my location.
This is a GPS feature where the device owner’s location can be broadcast to contacts on GPS.
Significant Locations (aka Frequent Locations)
Apple users have a feature logged on by default called Significant Locations which can be found within Settings/Location Services/System Services/Significant Locations. It also has Operating Systems calling this feature Frequent Locations. This records, as the name suggests, the places the phone user attends most commonly and records data when they were at this location, the time they arrived and left, and is represented on a map.
Investigations reveal most people are not aware of this feature and it is often turned on recording a lot of data that may be of great value to you. For example, the suspect says they have never been at an address of interest before, however, the Significant Locations data records data they were they three times over the past week and the exact time they arrived and left. This is strong evidence once you confirm they are the only person who uses that phone.
Secure Element Identifier (SEID)
The SEID relates to the chipset security and Near Field Communications (NFC) used in circumstances such as swiping to open a door, gain access to a location or using Apple Pay. This may be useful if the SEID number is recorded making a payment for a suspect transaction.
Software update
This shows the current version of the software as well as whether the device is currently up to date. This will be useful to the investigator in identifying vulnerabilities in the device which has not been updated to the current version of the operating system, leaving it vulnerable to a technical attack.
Software version
This is a version number of the software on the phone such as 16.5 on an iPhone. Click the number and another number appears such as 20F66. This latter number is what is called the Build Number which relates to internal releases of the application before it is released to the public. These numbers are related.
Songs
Music on the device. May be linked to an iTunes account which may be another source of data/evidence.
Service Provider Number
This records the name of the cellular service provider.
Short Message Service (SMS)
SMS is a text message. This will be valuable to an investigator as it provides an understanding of not only communication, but who the device owner is interested in communicating with and when. It also provides an understanding of the tone of a conversation and the relationship between certain people.
Storage
This identifies the amount of space being taken on the device by apps, photos, media etc. Opening each app will provide details on the size of the application and separately identify the size of the contents of the app. For example, the app may show the size of the data within the cloud storage email accounts providing the investigator direction as to what potential data volumes they may be able to access. It also lists when an app was last used and apps that have never been used which may also be useful information.
Subscriber Identity Module (SIM)
The SIM card stores data about the operations of a person’s mobile device. They are identified by the ICCID which is usually seen as the serial number recorded on the SIM card. Also located on the SIM card is the IMSI number which links the customer using the mobile device to the mobile network.
A SIM card can also contain SMS details as well as contacts from the user’s phone book.
Videos
Videos on the device. Depending on the investigation, this may be very valuable evidence of the suspect’s activity including providing a GPS location of where the videos were recorded and when. The topic of the video may also be of interest to the investigation. Like photos, videos record relationships between people.
Voice memos
Voice memos record events of interest to the device owner. Also, they provide a sample of their and other people’s voices should there be a need to obtain voice biometrics. These memos can be set to delete after a specific period of time such as one day, 7 days or 30 days.
VPN (Virtual Private Network)
This is a Virtual Private Network which is a secure encrypted tunnel that data can travel through. The user’s data goes from the phone to the VPN company which then directs it to the site being requested by the user.
For example, a user may wish to view a news site from their mobile device. The phone sends the web address to the VPN company which then directs it to the news site. The news site only sees that a request to view their material has come from the VPN site and sends the web page to the VPN site which then redirects it to the device user. This means there is no direct link between the device user and the news website.
Under the VPN tab is the name of the VPN being used which may be useful when a device has several VPN applications which can be used individually at different times.
The investigator may find a link between a threatening message on a social media site and a VPN site. For instance, an examination of the suspect’s device that has been located from separate inquiries, such as a marriage breakup where a suspect has been nominated, identifies that the suspect uses that same VPN provider. Checking the battery use can show that the suspect was using the device at the time the message was generated. This is not conclusive proof, but another piece of the investigation puzzle.
Website & App passwords
This is where passwords to online accounts accessed through the mobile device are stored. It is a password-protected site itself and the device credentials are required by the investigator.
Importantly, this can lead to new areas of inquiry as unknown online accounts can be identified and the access credentials to them obtained. Passwords used in this folder may be found to be passwords used across other devices not linked to the mobile device.
Wi-Fi address
This is very important as it shows a unique identifier of the device as it connects or attempts to connect to a Wi-Fi point. This is also known as the Media Access Control (MAC) address.
The MAC addresses are unique to a device, although they can use a separate private MAC address to assist in privacy over a network. Of value to the investigator, the MAC address is stored on every router that it attempts to connect with. So, if an investigator wants to know who was in a drug house over the proceeding hours, their digital forensic examiner can conduct an examination of the router and identify all the MAC addresses that connected, or attempted to connect, to the router. Sometimes, depending on the router, it will record the device name mentioned above such as “Bill’s iPhone alongside the MAC address which tells the investigator a little bit more information.
This is discussed further in Chapter 10.

Mobile device examination
A mobile device examination will be undertaken by a person with the appropriate qualifications. They will use specialist software such as Cellebrite [3] to conduct the examination. The quantity and value of the data recovered from the device will be reliant on the model of the examining device and license, whether the access password/codes have been obtained and the ability of the application to recover data.
To assist the examiner, a report detailing the background of the investigation and the circumstances of the device seizure will be of benefit.
Examples of details to include in the report are as follows:
- Make and model of phone.
- The physical location where the phone was found.
- State of the phone when found.
- Whether the phone was on and what was displayed on the screen.
- The date and time displayed on the phone.
- Photos taken of the phone, including open windows if unlocked.
- Notes of any identifying labels, markings, phone case/cover.
- Notes on the chain of custody.
- An explanation to the examiner regarding the circumstances of the device seizure and the evidence you are seeking. The examiner may be able to explain what other evidence the device can provide that the investigator is unaware of.
Key Takeaways
Key Takeaways
As we have seen, the phone itself can provide a variety of valuable information. A lot of the items discussed above may prove irrelevant to a particular investigation, but it is worth knowing these forms of evidence exist as they may be of use in other investigations.
Apart from the obvious locations of evidence such as GPS, photos, messages and contacts list, being able to identify which app is of most value to the person of interest is valuable in understanding how they use the device. Also, the battery usage provides interesting evidence in proving or disproving the device owner’s statement about how they use the device.
Accessing the evidence without the consent of the device owner/operator will depend upon the quality of the application used in the examination. Companies such as Cellebrite produce software designed for the examination of mobile devices and have developed ways to access data that other services cannot obtain.
Scenario
Sledge’s mobile phone is with him all the time and accumulates data that records his location as well as other aspects of his activity.
Examples of the evidence from Alex’s and Sledge’s mobile phones which may advance the investigation include:
- Address book linking the suspect to the victim.
- Alex’s and Sledge’s address books show their drug-dealing contacts. (In a real-world scenario, dealers would use encrypted phones and apps, however for the benefit of the scenario and showing what levels of data are available from a phone, the scenario reads they have not used an encryption service).
- Bank account details can be accessed through a court order with the bank separately.
- Battery usage shows what activity was undertaken on each device post the death of Alex. This will show the areas of Sledge’s initial interest in the phone of Alex including changing access credentials so he can access the device again without the requirement of knowing Alex’s password.
- Calendar of meetings.
- Cloud storage apps include direct access to the accounts via the mobile device.
- Date and time which can be synchronized against the laptop and other digitally connected devices within the scenes.
- Emails.
- Emergency contact details.
- Encrypted communications.
- Find My Friends feature activated which shows the close physical proximity of Sledge and Alex.
- GPS data.
- Health data showing steps taken in time blocks and blood pressure at the time of the activity leading up to and including the time of Alex’s death.
- Internet searches.
- Logs showing Sledge logged into Alex’s bank account once Alex was deceased. Separate bank inquiries will show details of the bank transfer.
- Logs showing the timeline of events involving the usage of both phones. Both Alex and Sledge are drug dealers, and these inquiries will be of relevance to the investigators alongside the homicide investigation.
- Make and model of phone.
- Media Access Control (MAC) of the Wi-Fi and Bluetooth.
- Messages and chat conversations.
- Name of device such as “Sledge’s iPhone”. This name may be located on a router the device has been connected to through Wi-Fi.
- Networks the devices have been connected to through Wi-Fi.
- Phone call records.
- Photos. Very useful for building victim and suspect profiles including connections.
- Service provider. This can lead to inquiries to confirm the registered names of the phones, their address as well as the payment details which may indicate a bank account that was previously unknown.
- Screen time. In this section, are the details of the first app accessed when the phone is activated. This app can be seen as the most important app of the device to the user. For example, a person may check their Facebook account many times during the day, and the fact that when they activate their phone, the first app they access is Facebook. This indicates the purpose of accessing the phone at that time is to view Facebook. If the app accessed first is regularly a secure, encrypted account, that would tell you that the app is particularly important to the user.
- Search history where the phrases “Lock picking houses”, “How to cut glass windows”, “How to kill someone” and “How to dispose of a body” are located.
- Significant locations. This app shows the locations the device user goes to regularly as well as the exact dates and times they were present. It is an extremely useful feature to place a person at a specific location and in a specific block of time once you have confirmed they do not let anyone else use their phone.
- SMS messages.
- Synced devices. Depending upon the make and model of the devices, activity on synced devices may be retrievable on other devices.
- Vehicles that the phone has been synced to. This will show a connection between the mobile device and Alex’s car which Sledge took after the homicide.
- Version: Operating System number.
- Videos: Very useful for building victim and suspect profiles including connections.
- Voice memos. Not commonly used, but there may be instances where Alex or Sledge wanted to record a conversation as proof of what was said.
Depending upon the make and model of the devices, activity on synced devices may be retrievable on other devices.
Some of these listed items are evidence of the phone itself and not its use. For example, the make and model of the phone and its OS version are not evidence of the commission of any offence but are evidence that the phone exists, and the court has knowledge of what type of phone it is. This is a small detail, but successful court cases are built on a foundation of the small details being thoroughly attended to present the most conclusive evidence.
Both Alex and Sledge were heavy users of their phones, and their phones can provide many sources of data as well as evidence of their location and activity.
A unique communication identifier for your connected device. For example, a laptop will have unique identifiers for ethernet (the physical blue cable), and wireless and Bluetooth connections.
A satellite system which devices can connect to and identify and find a precise location.
Skin tones and its response to ultraviolet light.
Medical ID
This is the number recorded on a Subscriber Identity Module (SIM) card. It is also a unique identifier of the SIM card which can be used to locate the region where a SIM card was purchased.
Used to identify and authenticate an account on mobile devices. This is a unique identifier of the device and is linked to the associated account.
A unique identifier burnt into a mobile device and cannot be modified.
Technology that allows multiple users to use the same communications channel at the same time.
Automatically fills a text box with pre-input data.
Technology used in making contactless payments whilst using Near Field Communication (NFC).
Near proximity connectivity standard. You may be familiar with using NFC when using your phone to make payments.
Version of an application or component of technology.
Short Message Service. A text-only messaging service.

